Hi there! In this multi-blog series, you will learn how to build a fully functioning and usable SOC using all open-source tools. I started working on this project because I wanted to learn SIEM. But how can anyone learn a SIEM tool without getting logs from endpoints and simulate different types of attacks on those endpoints to analyze attack scenarios.
So I decided not to just a learn a single SIEM but to build a whole SOC environment which would have a SIEM, EDR, XDR, Endpoints, Firewall, Case Management Solution, Threat Intelligence Platform and finally an Attacker Machine.
In this part, we will gather all the ISOs and Docker Containers for Client VMs, SIEM Tool, IR/Case management tool, Firewall. Below are the web links that you can use. Download everything and get ready to start setting up the Lab.
For Agents/Client Machines:
- Windows 10 Pro ISO : https://www.microsof … ownload/windows10ISO
- Ubuntu Desktop (you can use either LTS or Latest Rolling): https://ubuntu.com/download/desktop
Firewall
- OPNSense Firewall: https://opnsense.org/download/
SIEM
- Wazuh Docker Deployment: https://documentatio … l#deployment-options
Incident Response and Case Management Platform
- DFIR-IRIS Docker Deployment: https://docs.dfir-ir … est/getting_started/
Setting up a Lab
In order to build a SOC we will need an environment where we can configure and play with different tools. Its better to keep something like this isolated on Virtual Machines or on Docker Containers so that they won’t mess with our primary host. To create a lab for this purpose I would suggest to invest in a powerful workstation (only if it is easily possible. I know its expensive). As I can’t afford to build a workstation now I am using my primary laptop. On it, I am using Virtualbox for all the virtual machines we need (for endpoints, firewalls) and I will be running docker containers for SIEM other tools on my host system. I know what I said earlier that we should keep this isolated from our host. But I simply don’t have enough RAM to fire up more than 5 Virtual Machines on Virtual Box at the same time.
My System Specifications (Minimum Requirements)
- RAM: 16 GB DDR5 4800 Mhz
- Storage: 512 GB
- CPU: 12th Gen Intel(R) Core(TM) i7–12700H (20) @ 4.7z
- GPU: GeForce RTX 3050 Ti Mobile
- Host OS: Garuda Linux (Arch Based)
- Virtualization Software: VirutalBox
Virtual Machines we need:
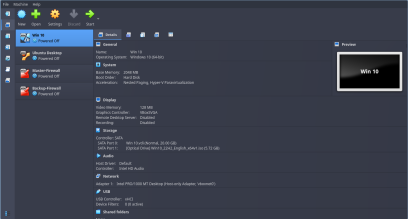
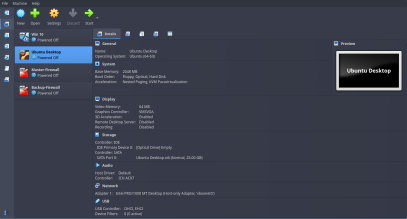
- First, create 2 VMs; a Windows 10 Pro and an Ubuntu Desktop. Now both these VMs will require at least 2 GBs RAM & 25 GBs Disk Space each to work properly
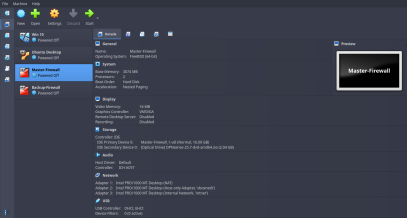
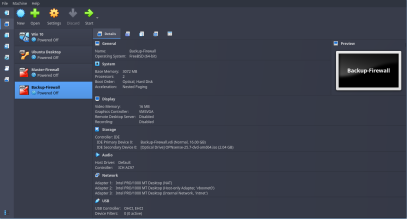
- Now, create 2 more VMs for a Master Firewall and a Backup Firewall (These will work using pfsync protocol to create a High Availability Setup. We will set up that up in next parts). Install OPNsense Firewalls in them
Network Setup:
This is the confusing part, I suggest you read every word carefully and don’t rush❗
VirtualBox Network Settings:
- First, Open Virtualbox and go to it’s Network Settings.
- Under “Host-only Networks” if there is not a default network created by virtualbox, create one!
- If a network exists, then check its IP settings. There must be a DHCP Server enabled which will automatically assign IP addresses to VMs. (For e.g. Network Gateway: 192.168.56.0 and DHCP Server Address: 192.168.0.100)
For Windows 10 Pro and Ubuntu Client Machines:
Go to VM Settings then Network settings. Here, under Adapter 1 click on Enable Network Adapter. Then, For “Attached to” drop-down menu, select Host-Only Adapter.
The reason why I am using a single adapter with Host-only adapter settings here is because I will be using my host machine for SIEM and Incident Response/Case Management tools. So, these VM’s should be able to talk (send logs data) to my host machine.
If you want to check if the VBox config is right or not, then check these screenshots below to verify if you have set it up correctly or not.
For Wazuh and DFIR-IRIS
To install Wazuh and DFIR as Docker Single Compose Stacks, simply follow their official documentation which I have given above in the web links. It is really easy! There will be no network setup needed as we will be using our Host Machine for both these services. Only DFIR-IRIS will require a different port to run on for its web interface. It will probably spit out an error while firing up the docker containers that the default 443 port is being used by a different service which makes sense because Wazuh Dashboard uses 443 by default.
So to change the default port for IRIS:
- Go to DFIR-IRIS Directory and edit docker-compose.base.yml file
- Find ports section, remove default line and instead write:
ports: - 8443:443
This will map the Port 8443 to 443. Then save the file and restart docker containers. Now IRIS should work fine on Port 8443.
OPNsense Firewalls Network Adapter Settings
Now, both the Master and Backup Firewalls will require 3 Network Adapters.
- Adapter 1 : NAT Mode (This adapter is for WAN, so that our Client VMs can connect to the network through Firewall)
- Adapter 2 : Host-Only Adapter (This is for LAN. We will give a static IP to the firewall where we can also handle firewall settings using its web interface)
- Adapter 3 : Internal Network (This is for High Availability Setup, basically to sync with the other firewall)
This is how Vbox settings page looks like for both Firewalls.
————————————————————————————————————————————————————————-
That’s it for this part!
In the next part we will go over
- Firewall Setup, Custom Rules
- Network Connectivity Test
- Wazuh Agent Installation & Integration to Wazuh Server
- MISP Setup (Tool for Threat Intelligence)
Till then, Cheers!☕